The new Amazon Inspector
The new Amazon Inspector offers customers the following capabilities:
- Easy to Enable (literally two clicks)
- AWS Organizations (Multi-Account) Support
- Continuous Vulnerability and Network Reachability Scanning
- Utilizes SSM Agent (no longer requires a standalone agent)
- Findings are Scored
- Findings can be Suppressed
- Remediated Findings are Automatically Closed
- Dashboard has been Redesigned
- In addition to EC2 Scanning, ECR Stored Container Images can be Scanned
- Available in All Commercial, GovCloud and China Regions
Let’s explore each of these capabilities!
Easy to Enable (literally two clicks)
As depicted in the screenshot below, individual accounts can enable the service by clicking Enable, optionally selecting EC2 or ECR container scanning options:
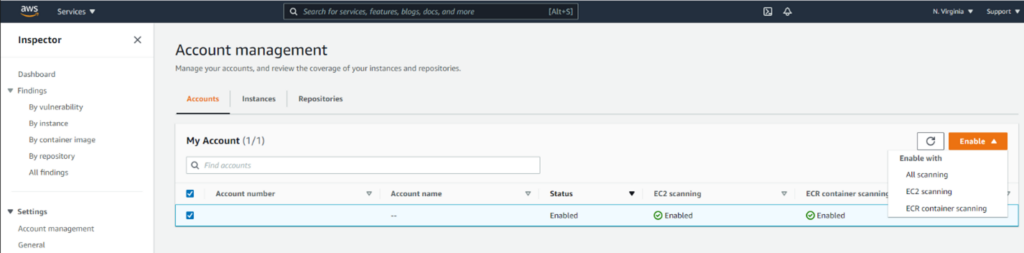
As soon as it’s enabled, any instance with a recent SSM Agent version, and a properly configured IAM Role, starts to automatically scan:
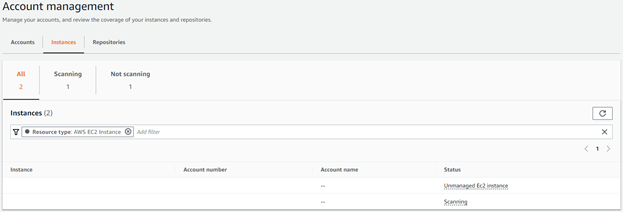
Pictured above is an “Unmanaged Instance”, which does not have a running SSM Agent or a properly configured IAM Role. This state (and other states) are not only visually depicted, to identify coverage gaps, but an event is emitted to EventBridge as well (more on this later!).
Compared to Amazon Inspector Classic, which relied on tags to specify in-scope instances, all instances are in-scope by default.
AWS Organizations (Multi-Account) Support
Similar to GuardDuty, Amazon Inspector supports the automatic enablement of scanning for new member accounts that are part of an Organization:
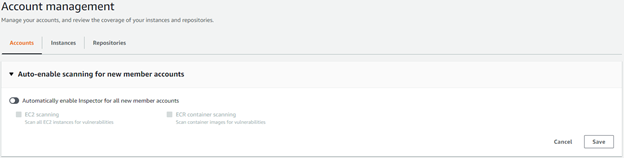
Additionally, individual account status is clearly depicted:
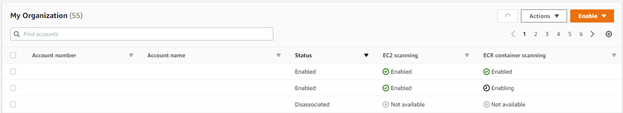
Both of these capabilities further support the identification of coverage gaps – by ensuring new accounts are enabled by default (and subsequently instances and ECR container scanning enabled automatically and accounts in which the feature is disabled are easily identified, as displayed above.
Compared to the previous version, in which individual accounts configured and emitted events, configuration and events can now be centrally administered and emitted.
Continuous Vulnerability and Network Reachability Scanning
Rather than relying on a scheduled based scanning, scanning of instance and container vulnerability, and instance network reachability is continuous, avoiding potential gaps, in which a vulnerability or a configuration resulting in broad network reachability exists between scan intervals.
An example of this would be the detection of subsequent vulnerabilities days apart:
![]()
Utilizes SSM Agent (no longer requires a standalone agent)
The previous version of Inspector required a separate agent to be installed, which was installed either manually, bootstrapping, included in an image, or deployed via SSM, by the Inspector service. This version utilizes the SSM Agent, reducing the overall impact on system resources.
Findings are Scored
In addition to providing the NVD/CVVS or Vendor Score, Inspector provides it’s own score, based on the NVD/CVVS or Vendor Score, Adjusted for the Compute Environment. For example, if the Compute Environment is not Internet Accessible, the Score may be Reduced. An example of this is shown below:
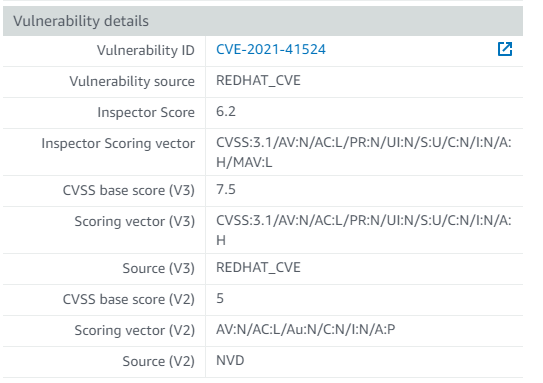
In the Previous Version of Inspector, the NVD/CVVS or Vendor Score was displayed.
Findings can be Suppressed
Finding can be suppressed using similar rule notation as Guard Duty to suppress findings that may not be relevant to your organization, for example, suppressing findings with an Inspector score less than or equal to 5 would be configured like this:
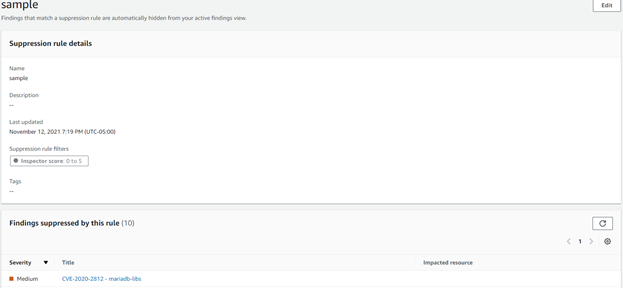
In the previous version, findings could not be suppressed.
Remediated Findings are Automatically Closed
Remediated findings are automatically closed when they are no longer detected. Example of this would be updating a vulnerable library or removing an excessively permissive Security Group grant. An example of this is below:
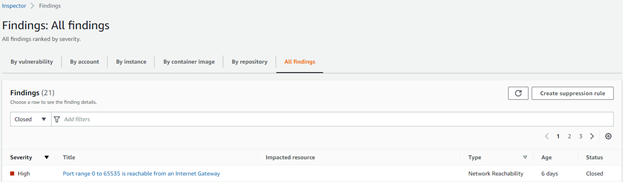
In the previous version, findings did not have a status.
Dashboard has been Redesigned
With the simplification of Amazon Inspector configuration (elimination of assessment targets, templates and schedules), and the addition of the new features described above and below the dashboard has been redesigned:
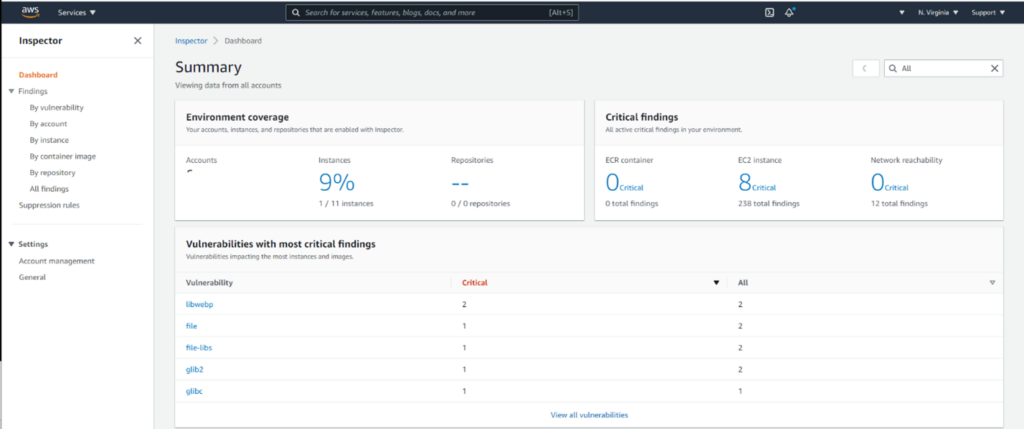
In addition to EC2 Scanning, ECR Stored Container Images can be Scanned
ECR Stored Container Images can be Scanned, with findings included in the same Dashboard and emitted to the EventBridge:
Previously, Inspector did not support Container Scanning.
Available in All Commercial, GovCloud and China Regions
Finally, Inspector is available in All Commercial, GovCloud and China Regions whereas previously Inspector was available in _most_ regions and GovCloud, with some exceptions.
In Conclusion, the new Amazon Inspector offers significant advantages over the previous version of Inspector, eliminating complex configurations, adopting an opt-in by default approach to scanning and eliminating potential gaps in workload and image scanning.
We are looking forward to leveraging it within our organization, along with SecurityHub and EventBridge based integrations to automate common vulnerability identification, triaging, mitigation/remediation and reporting activities. One such example of that can be found here: https://aws.amazon.com/blogs/apn/sending-amazon-inspector-common-vulnerabilities-and-exposures-findings-to-the-servicenow-secops-module/
– Patrick Hannah, CTO, CloudHesive


