
Using VPC Flow Logs to Troubleshoot Network Connectivity to Your EC2 Instance
Anthony Palmer, Senior Cloud Engineer at CloudHesive
Here at CloudHesive we encounter all types of AWS questions from our customers. One of the most common questions our engineering and support staff encounter daily is, “Why can’t I connect to my EC2 instance?” or “Why can’t I connect to my RDS?
The first thought from any AWS engineer should be security groups, maybe on a rare occasion it is a route table issue. So how do we go about and determine what the actual issue is? Lucky for us, AWS logs all network traffic in VPC flow logs. Combine the VPC flow logs with a custom CloudWatch filter and you can easily trace packets across your AWS environment.
Step 1: Identify the ENI (Elastic Network Interface) of the destination EC2
From the EC2 screen take note of the Interface ID for the Network Interface as well as the IP address. In this example we will be accessing a sandbox server from over the internet.
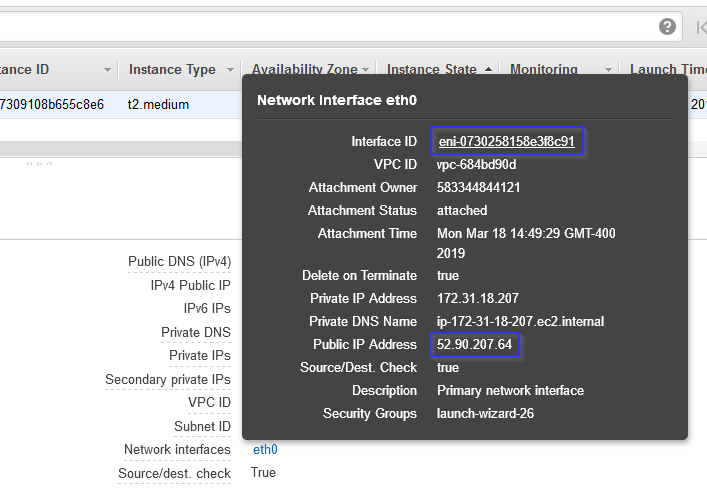
Step 2: Select the Network Interface and go to Flow Logs
*If Flow Logs are not enabled this tip won’t work
Step 3: Drill into the VPC Flow Logs and search for your ENI within CloudWatch
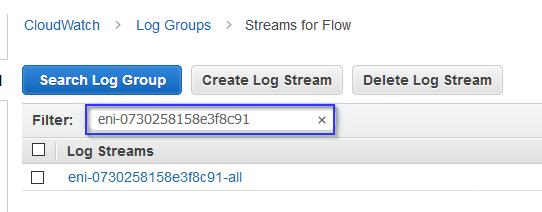
Step 4: Input a custom filter within search bar
[version, accountid, interfaceid, srcaddr, dstaddr, srcport, dstport, protocol, packets, bytes, start, end, action, logstatus]
Step 5: Adjust the filter to troubleshoot connectivity
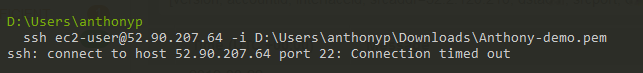
In this example we are trying to SSH into a Linux server from the AWS Workspace. We have removed all security group entries, so our access should be denied when SSH is attempted. The filter below filters on the source address, being the public IP of our Workspace and the port being 22 or SSH.
[version, accountid, interfaceid, srcaddr=52.2.120.210, dstaddr, srcport, dstport=22, protocol, packets, bytes, start, end, action, logstatus]
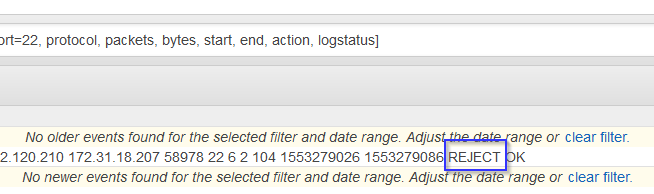
Step 6: Adjust the security group then the CloudWatch filter
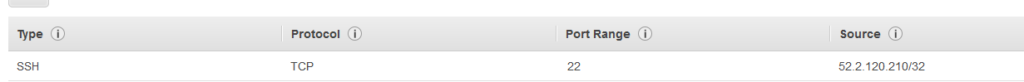
Now we can SSH into the Linux server.
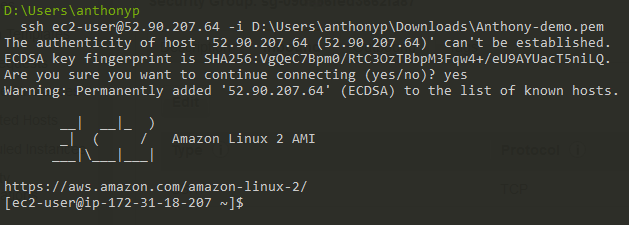
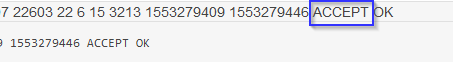
The CloudWatch flow logs now show an ACCEPT!
If you’re still unclear on how to connect your EC2 or RCD, reach out to the CloudHesive team today. Give us a call today at 800-860-2040 or fill out our online contact form.
[/fusion_text][/fusion_builder_column][/fusion_builder_row][/fusion_builder_container]


