A new discovery by a Brazilian Infosec research group called Morphus Labs should (once again) make you think twice about clicking on any unsolicited links. Dubbed “Mamba,” the new ransomware strain, like the snake it was named after, strikes with a paralyzing strength, able to lock down full disks instead of just individual files. Using an open source tool called DiskCryptor, it’s able to do great damage by deeply encrypting all the data found on the target machine’s hard drive.
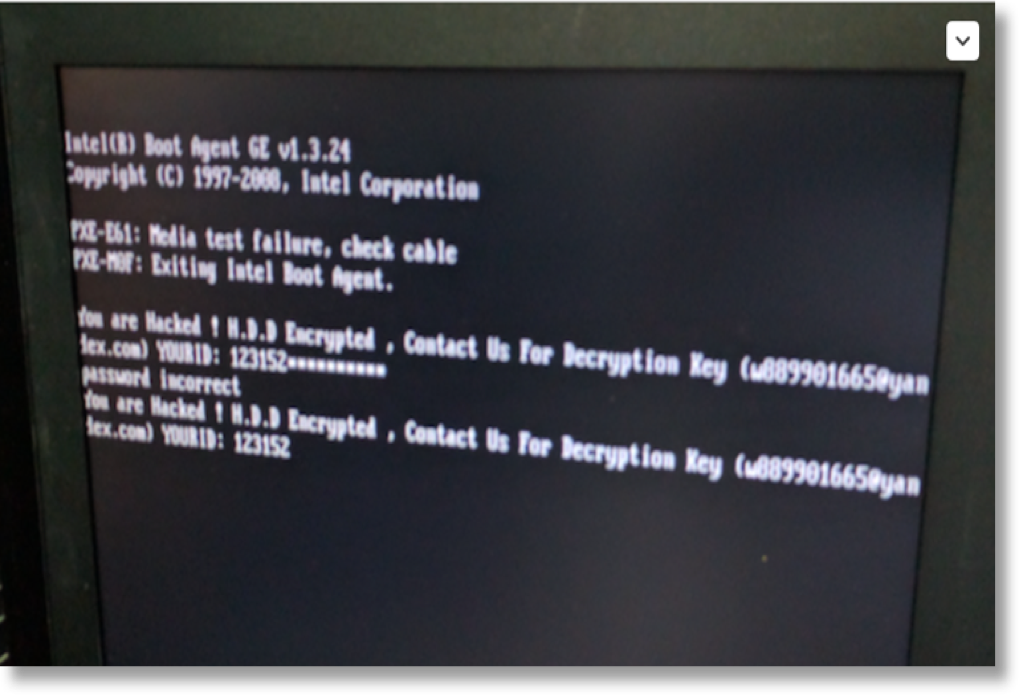
Mamba is very similar to fellow ransomware variant Petya, both of which use a disk-level encryption system, which seems to be a growing trend in the rapid spread of ransomware. “You Are Hacked,” says the message left by Mamba, along with a number victims are expected, via a unique ID, to call to find out where to pay the bitcoin worth of ransom (worth around $600) and get the private decryption key. Actually, the full message goes something like, “You are Hacked ! H.D.D Encrypted, Contact Us For Decryption Key ([email protected]) YOURID: 123152” (as seen in the image below):
This latest ransomware strain blocks the machine’s OS from even booting up and overwrites the boot disk master boot record, or MBR replacing it with a custom MBR that displays the ransom note asking for the decryption password. As soon as the malware variant is introduced on the targeted machine, it will reboot, but before the reboot, Mamba installs itself as a fake defragmentation service via Windows, which looks like the image at left.
Renato Marinho of Morphus Labs and his team have been working around the clock to counteract the insidious lock-down proposed by Mamba. He remarks, in a post on LinkedIn Pulse: “We found Mamba last September 7, during an incident response procedure for a multinational company that had some servers compromised by this malware in Brazil, USA and India subsidiaries.”
Marinho goes on to say that the decryption password may be the same for all victims of Mamba, also known as HDDCryptor, or that it may be something related to the victim’s environment, such as a hostname, or something similar. The Morphus Labs team has not yet located the infection vector, but they are still at it. We will try to update you on Marinho’s team’s progress.

In the meantime, as is the case with all of our messages on ransomware, we advise never paying the ransom, but instead letting an expert in malware infection lead a step-by-step analysis and countermeasures implementation to bypass and ultimately discard the ransomware from your computer. Also, don’t click on any unsolicited links, and have only the best antivirus software running on your network and all devices.
Let the Cybersecurity Experts Handle It
If you need further advice about cybersecurity and ransomware, CloudHesive is a proven leader in providing IT consulting and cybersecurity. Contact one of our expert IT staff at (800) 860-2040 or send us an email at [email protected] today, and we can help you with all of your cyber safety, defense, and security questions or needs.


